In simple words, DDOS means Distributed Denial of Service, DDOS is a type of attack where multiple botnets or internet devices are trying to access your system.
These botnets contain some malicious program in it which is very harmful to your system or server.
Basically in a DDOS attack, the hacker sends lots of unwanted, unspecified, unrelated traffic to crash our website or system.
There are 3 types of DDoS Attacks:
- Volume-based attacks
- Protocol attacks
- Application layer attacks
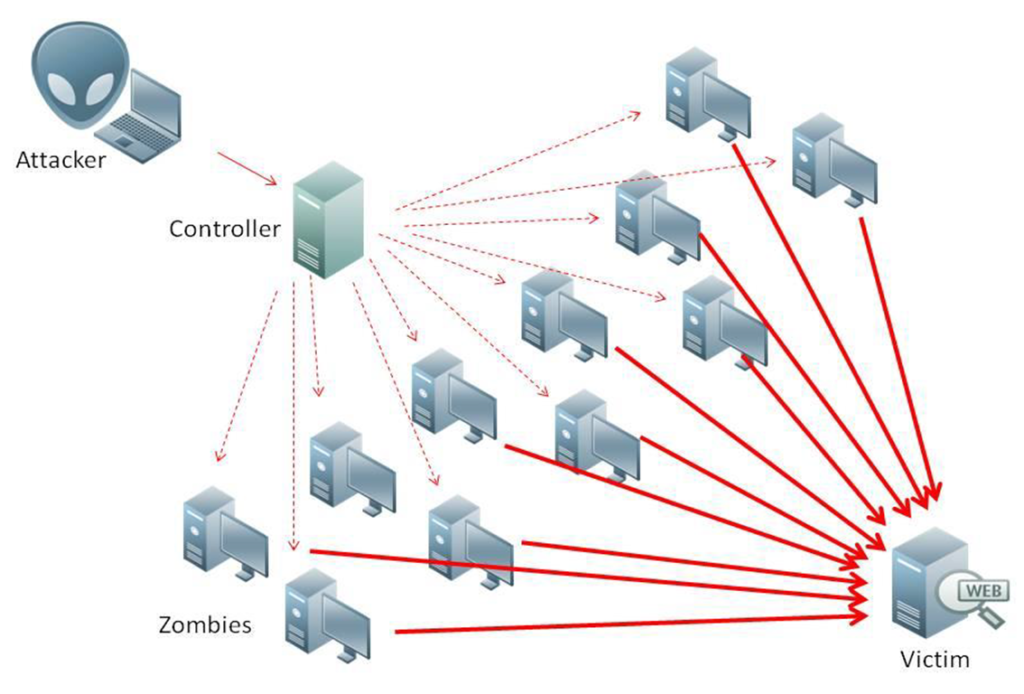
How DDOS Attack Works
A DDOS can be performed by an attacker where an attacker is trying to get control of a computer and other internet devices(IoT) and convert them into a bot. The attacker then has indirect control across the group of bots, which is called a botnet.
when every botnet has been established then the attacker is able to send commands to every botnet When the IP address of a victim is targeted by the botnet, each bot will respond by sending requests to the target, potentially causing the targeted server or network to overflow capacity, resulting in a denial of service to normal traffic. Because every bot is a genuine Internet device, separating the attack traffic from regular traffic can be tricky.
Recent DDOS Attack
- GitHub (February 2018) A popular online code management service used by millions of developers, GitHub is used to high traffic and usage.
- Dyn (October, 2016)
- BBC (December, 2015)
- Spamhaus (March, 2013)
- Bank of America/JP Morgan Chase/US Bancorp/Citigroup/PNC Bank (December 2012)
DDOS Tool
- HULK
- Tor’s Hammer
- Slowloris
- LOIC
- XOIC
- DDOSIM
- RUDY
- Pyloris
Conclusion
The tools that are mentioned in this article is the most useful and popular. These tools are good sources for performance and security testing.
To conclude, HULK will be a good tool for research purposes. LOIC and XOIC are easy to use. LOIC can be used for testing. RUDY and PyLoris are also designed particularly for testing purposes.
